
Photo by Jefferson Santos on Unsplash
7 Cybersecurity Threats You Must Know as a Web Developer
Maintaining solid cybersecurity is critical in web development. Learn about the seven most common attacks that threaten your online systems.
The Web Today
The internet has come a long way from its initial launch. Consumers have become reliant on the vast sea of incredible technologies they use every day to improve their work and home lives. Developers know that beneath the shiny surface of these powerful technologies is a complex network of hardware and software, making it all work.
Along with the advanced software most of us take for granted, lurk thousands of cyber criminals working overtime to get their hands on users’ data, networked systems, and money. Keeping on top of these threats is a full-time job.
The Effects of Cyber Crime
Cybercrime affects everyone. Whenever a supply chain gets hit, consumers are affected by shortages and high prices. When a government agency or retail corporation is attacked, a data leak can lead to identity theft and the loss of millions.
Security specialists and web developers are also greatly affected when an attack occurs. You must spend hours determining the damage, tracing the entry route, and patching the holes.
When attackers use a mobile app to steal funds, the web developer who created it may be held responsible or at least experience a dent in their reputation.
Web Threats
As a web developer, you must have a good handle on all the current web threats out there so you can prevent them or quickly respond to them. There are various threats that are quite common but others that are newer and more complex. To stay on top of your game and secure your websites and apps, be sure to educate yourself on all the current threats so you can prepare for anything.
The most important thing to understand is that no code is bulletproof against threats. At some point, hackers will find a way around any code, security protocols, firewalls, and other protections, and they will breach your app. Therefore, you must be diligent about constantly monitoring your work, scanning for new threats, and being ready to pivot to meet the demand. Major examples of these web threats include:
Cross-Site Scripting (XSS)
Cross-site scripting is a serious threat affecting roughly 66% of all web applications on the market today. Hackers can steal user credentials, intercept sessions, and even bypass multi-factor authentication using cross-site scripting. There are three main types of XSS attacks, Stored XSS, DOM XSS, and Reflected XSS. All three are incredibly effective and dangerous as they exploit the vulnerabilities within the software and attempt to take over the user’s browser.
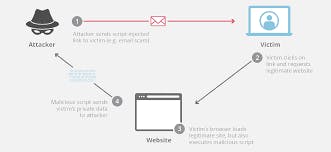
One way to avoid these vicious attacks is to develop your web apps using Django) or Ruby on Rails which includes algorithms to block XSS. For DOM XSS attacks, you can use context-sensitive encoding whenever the browser is modified.
Sensitive Data Exposure
Sensitive data exposure is every company’s worst nightmare. Unfortunately, data breaches have become widespread across every industry, and no business, regardless of size, is safe.
Cybercriminals are skilled at breaking into software and networked systems, but as a developer, you must also consider how you are securing sensitive assets. If you leave the door open, hackers will come in.
When storing personal or sensitive information online, such as customer names, addresses, phone, email addresses, credit card numbers, employee dates of birth, social security numbers, etc., you should employ strong encryption policies to protect and secure the information from prying eyes.
Additionally, securing the network against man-in-the-middle attacks will help keep devices clean and secure. Remember, data can be intercepted at any time; if it is encrypted, the hacker will have a much harder time using it for anything. Keep in mind third-party vendors and partners and their security as well. Anyone in your supply chain can be the weak link that leaks data.
Insecure Authentication
All online resources, websites, and apps use authentication to allow users to log in. However, different types of authentication are not created equal. Usernames and passwords are the most common, but they are also one of the most vulnerable to hackers. Using tools like brute force, credential stuffing, and bots, they can unlock even long secure passwords gaining entry to user accounts. The bottom line is passwords are not a viable solution for the future.
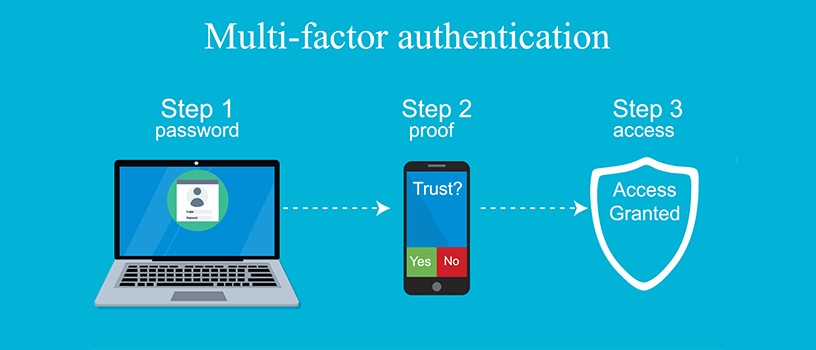
A better option is to build integration into your apps and websites for multi-factor authentication or, even better yet, biometrics like fingerprint and face ID. Remember to safeguard session tokens and use SSL to protect access credentials and session identifiers. If you take the time to secure the authentication process, you may have an easier time preventing attackers from getting into the system completely. Be sure to timeout session IDs once the user has logged out and invalidate the session value so it cannot be used if left open.
Weak Access Control
With your authentication system, you also need to focus on access control. The two operate interdependently to protect specific areas of the system, but often, even when authentication works, access control can break down, exposing sensitive data or vulnerable configuration settings.
Hackers often target access control once they have obtained a specific user account, elevating the user’s privileges to an administrator so they can access settings, configuration parameters, and exploit entire systems. These criminals use sophisticated scanning tools to find vulnerable access control. Sometimes they can take control by changing the account ID in the URL and don’t even have to log in to access anyone’s account. Don’t overlook this critical section of your web app.
SQL Injection
SQL injection is another very real threat to be concerned with. Some others to watch out for are Path and NoSQL injection. Bad actors inject malicious code into your web pages to access databases, change information, steal data, or add malware to your code. These types of attacks may use shell commands, system calls, and databases.

If you don’t properly secure your code validating all inputs and outputs, a hacker could easily affect your program using an injection attack. Attackers often use scripts written in Perl or Python to execute this type of invasion. Be sure to implement data cleaning, input validation, character-escaping, parameterized queries, and stored procedures to avoid these types of hacks. Additionally, do not connect your database with an account that has root access. Otherwise, you leave the entire system vulnerable. You can also install a web application firewall to help avoid injection threats.
XML External Entities Attack(XEE)
When using XML (Extensible Markup Language) in your web project, be aware that XML processors can be vulnerable to XEE attacks. Cybercriminals can use these processors to inject malicious content into your code and wreak havoc with the system. They can also cripple XML processors using denial-of-service attacks and then access your system and files or even execute remote requests from the server. Sometimes they alter the data in your XML files to deliver the payload to other users.
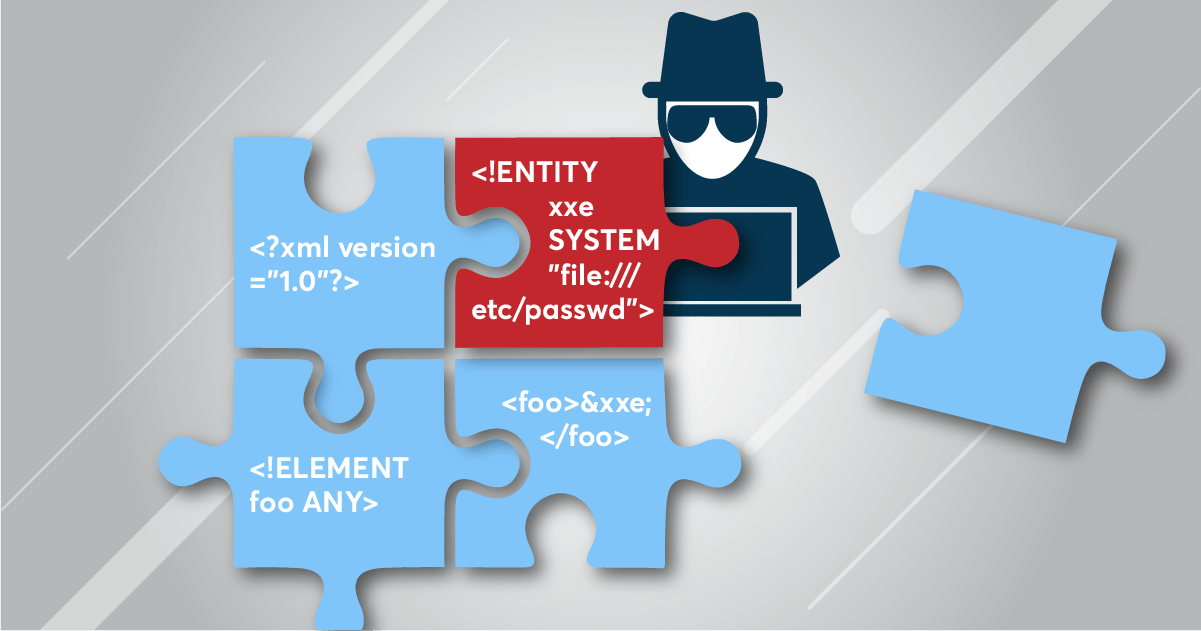
Be sure to update all your XML libraries as soon as they are patched for any vulnerabilities. Also, disable XML external entity processing in XML parsers. Consistent logging and monitoring of all web files is another safeguard that can help you prevent these attacks or respond quickly if they do occur.
Using Components with Known Vulnerabilities
Developers and coders love to use snippets of code or components that work well. It saves time and money not to have to build it from scratch. However, these components could come with gaping holes ready to welcome in the next hacker.
Your entire web app is only as strong as its weakest link.
Modular systems like WordPress allow developers to extend the functionality of websites quickly and easily; however, if these plugins are not coded correctly, they can expose your entire site to danger.
There are dozens of horror stories on the web about websites that were hacked due to a simple chat add-on or payment plugin. Therefore, before using any packaged code or module and integrating it into your program, examine it carefully for any flaws. Older code may be more vulnerable to exploits than new programs. Try to limit using as few of these components or dependencies as possible and rely on your own code for protection.
For additional protection, remove all outdated or unused dependencies. If you can, replace weaker plugins and modules with better-coded ones. Only download libraries and code snippets from the source. Avoid downloads at public repositories; the files could be corrupted or laced with malware.
The Bottom Line is Vigilance
Hackers attack web applications and websites every day to steal sensitive information, blackmail people, and steal money or credentials. Sometimes, these criminals look to create chaos in society or ruin a company’s reputation. Regardless of the goal, cybercrime can cause a lot of damage to a company, clients, vendors, and employees. The effects are far-reaching to our global economy, products, and consumers.
Hackers rarely attack in one day. Therefore, while they are biding their time doing homework and looking for vulnerabilities to exploit, you can be solidifying your systems. Be sure to implement comprehensive logging of all changed files, access, and updates. That way if anything changes, you will be notified and can investigate, potentially avoiding disaster. If you cannot set up access alerts, then put in place a firm monitoring schedule to keep a close eye on all your code, systems, and access breaches. As a side note, store access logs outside the root server so hackers cannot manipulate them to remove any evidence of their intrusion.
You must do all you can to protect your online creations from the myriad of new and existing threats. At least now, you know about the top 7 threats to watch out for and can use this knowledge to protect your software and apps from cybercrime.

